Study shows 58% of malware families sold as service are ransomware
By IANS | Updated: July 2, 2023 16:45 IST2023-07-02T16:41:32+5:302023-07-02T16:45:06+5:30
New Delhi, July 2 A new study has revealed that 58 per cent of malware families sold as ...
Study shows 58% of malware families sold as service are ransomware
New Delhi, July 2 A new study has revealed that 58 per cent of malware families sold as a service are ransomware.
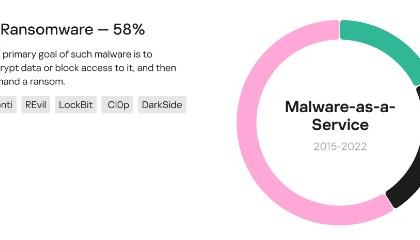
The Kaspersky Digital Footprint Intelligence team presented a study that unveiled ransomware as the most widespread Malware-as-a-Service (MaaS) over the past seven years.
The study is based on research conducted on 97 malware families distributed on the dark web and other resources. Moreover, the researchers discovered that cybercriminals often hire infostealers, botnets, loaders and backdoors to carry out their attacks.
MaaS is an illicit model of business involving the leasing of software to carry out cyberattacks.
Clients of such services are typically provided with a personal account via which they can control the attack as well as technical support. It lowers the initial threshold of expertise that would-be cybercriminals must meet.
Experts analysed malware families' sales volumes, posts, mentions, discussions and more to identify popular MaaS types.
Ransomware emerged as the top MaaS type, accounting for 58 per cent of all distributed families from 2015 to 2022.
Cybercriminals can subscribe to Ransomware-as-a-service (RaaS) for free. After they become partners in the programme, they have to pay for the service after each successful attack.
"Cybercriminals actively trade illicit goods and services, including malware and stolen data, over the shadow segments of the internet.
Organisations can protect themselves from MaaS by always keeping software updated on all the devices to prevent attackers from infiltrating the network by exploiting vulnerabilities and by using the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors.
Disclaimer: This post has been auto-published from an agency feed without any modifications to the text and has not been reviewed by an editor
Open in app